[ad_1]
GitHub Actions and Azure digital machines (VMs) are being leveraged for cloud-based cryptocurrency mining, indicating sustained makes an attempt on the a part of malicious actors to focus on cloud sources for illicit functions.
“Attackers can abuse the runners or servers supplied by GitHub to run a company’s pipelines and automation by maliciously downloading and putting in their very own cryptocurrency miners to achieve revenue simply,” Development Micro researcher Magno Logan mentioned in a report final week.
GitHub Actions (GHAs) is a steady integration and steady supply (CI/CD) platform that enables customers to automate the software program construct, check, and deployment pipeline. Builders can leverage the characteristic to create workflows that construct and check each pull request to a code repository, or deploy merged pull requests to manufacturing.
Each Linux and Home windows runners are hosted on Standard_DS2_v2 digital machines on Azure and include two vCPUs and 7GB of reminiscence.
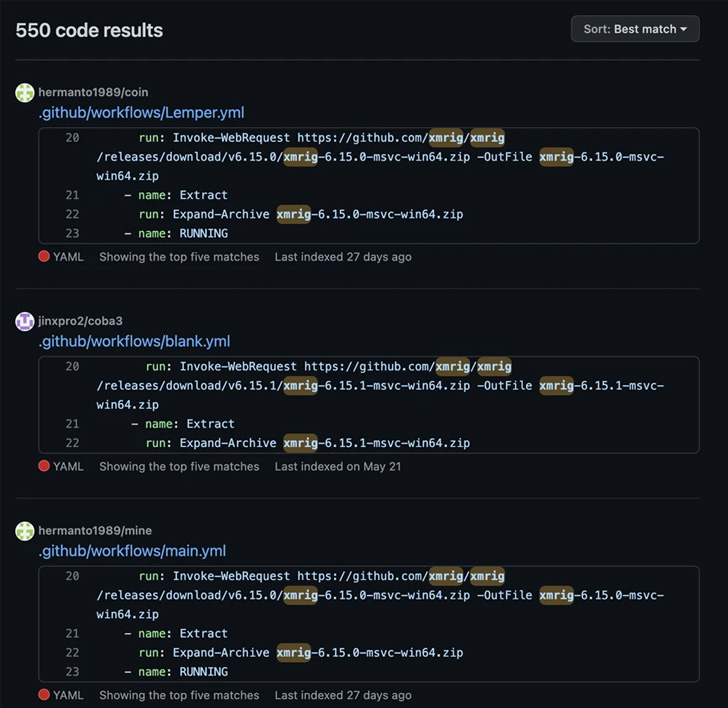
The Japanese firm mentioned it recognized no fewer than 1,000 repositories and over 550 code samples which are benefiting from the platform to mine cryptocurrency utilizing the runners supplied by GitHub, which has been notified of the difficulty.
What’s extra, 11 repositories have been discovered to harbor comparable variants of a YAML script containing instructions to mine Monero cash, all of which relied on the identical pockets, suggesting it is both the handiwork of a single actor or a gaggle working in tandem.
“For so long as the malicious actors solely use their very own accounts and repositories, finish customers shouldn’t have any trigger for fear,” Logan mentioned. “Issues come up when these GHAs are shared on GitHub Market or used as a dependency for different Actions.”
Cryptojacking-oriented teams are identified to infiltrate cloud deployments by way of the exploitation of a safety flaw inside goal techniques, equivalent to an unpatched vulnerability, weak credentials, or a misconfigured cloud implementation.
A few of the outstanding actors within the unlawful cryptocurrency mining panorama embrace 8220, Keksec (aka Kek Safety), Kinsing, Outlaw, and TeamTNT.
The malware toolset can be characterised by way of kill scripts to terminate and delete competing cryptocurrency miners to greatest abuse the cloud techniques to their very own benefit, with Development Micro calling it a battle “fought for management of the sufferer’s sources.”
That mentioned, the deployment of cryptominers, in addition to incurring infrastructure and power prices, are additionally a barometer of poor safety hygiene, enabling menace actors to weaponize the preliminary entry gained by way of a cloud misconfiguration for much extra damaging targets equivalent to knowledge exfiltration or ransomware.
“One distinctive facet […] is that malicious actor teams don’t solely must cope with a goal group’s safety techniques and employees, however additionally they must compete with each other for restricted sources,” the corporate famous in an earlier report.
“The battle to take and retain management over a sufferer’s servers is a serious driving power for the evolution of those teams’ instruments and strategies, prompting them to consistently enhance their capacity to take away opponents from compromised techniques and, on the similar time, resist their very own elimination.”
[ad_2]
Supply hyperlink